That’s surprising that for all these years I didn’t know about Wireshark MATE:
MATE: Meta Analysis and Tracing Engine
What is MATE? Well, to keep it very short, with MATE you can create user configurable extension(s) of the display filter engine.
MATE creates a filterable tree based on information contained in frames that share some relationship with information obtained from other frames. The way this relationships are made is described in a configuration file. The configuration file tells MATE what makes a PDU and how to relate it to other PDUs.
I found it very useful when analysing Diameter logs. It helps to solve eternal problem: how to get whole diameter session when you know only MSISDN (or Result-Code or an other AVP which is not present in both CCR and CCA and the only way to bind CCR and CCA is Session-Id).
The answer is MATE.
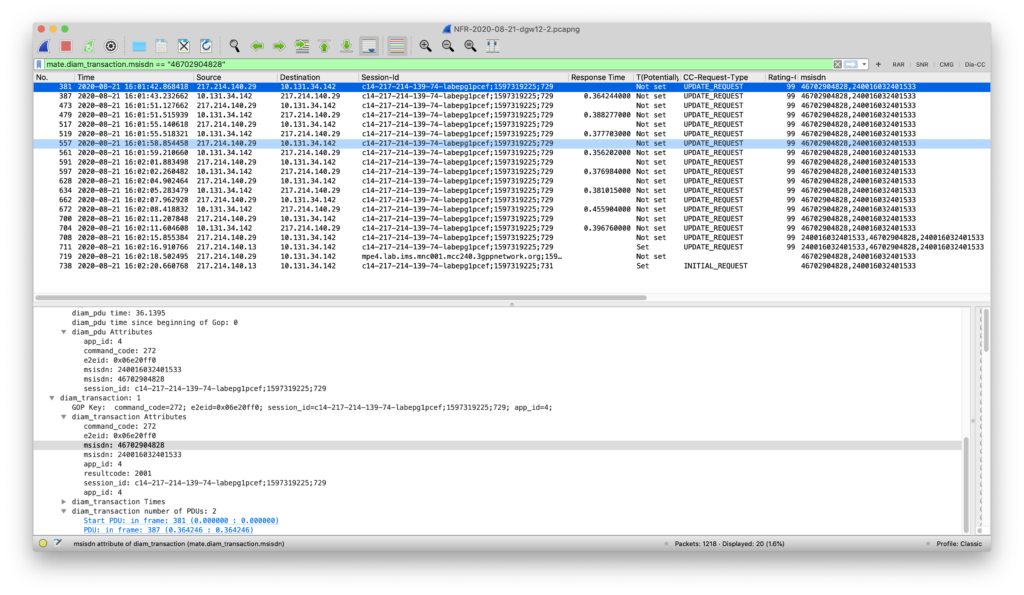
If I want to search for my MSISDN, I can use this filter:
mate.diam_transaction.msisdn == "46702904828"
In result, Wireshark will filter all CCR and CCAs where this subscriber is involved:
How to configure Wireshark for Diameter with MATE?
Lucky, MATE is built-in into current version of Wireshark. All we need to do is to create configuration and set it up in Wireshark preferences
MATE cfg file for Diameter
As I wanted to filter using MSISDN (actually Subscription-Id) and Result-Code, both needs to be extracted.
We will be binding messages using Session-Id, App Id and End-to-end Identifier
(credits needs to go to an anonymous poster to Wireshark forum; I’ve modified this file slightly adding MSISDN and Stop conditions)
// Create a "diam_pdu" that contains various pieces of the processed Diameter
// message.
Pdu diam_pdu Proto diameter Transport ip {
Extract command_code From diameter.cmd.code;
Extract app_id From diameter.applicationId;
Extract session_id From diameter.Session-Id;
Extract e2eid From diameter.endtoendid;
Extract resultcode From diameter.Result-Code;
Extract msisdn From diameter.Subscription-Id-Data;
Extract flag From diameter.flags.request;
Extract request_type From diameter.CC-Request-Type;
};
// Then create a GOP (Group Of Pdus) where the each GOP contains all the PDUs
// (msgs) that whose command_code, app_id, session_id, and e2eid match.
Gop diam_transaction On diam_pdu Match (command_code, app_id, session_id, e2eid) {
Start();
Stop(flag=0,request_type=3);
// Store the result code in the GOP
Extra(resultcode, msisdn);
};
Done;
Save the file somewhere on the disk.
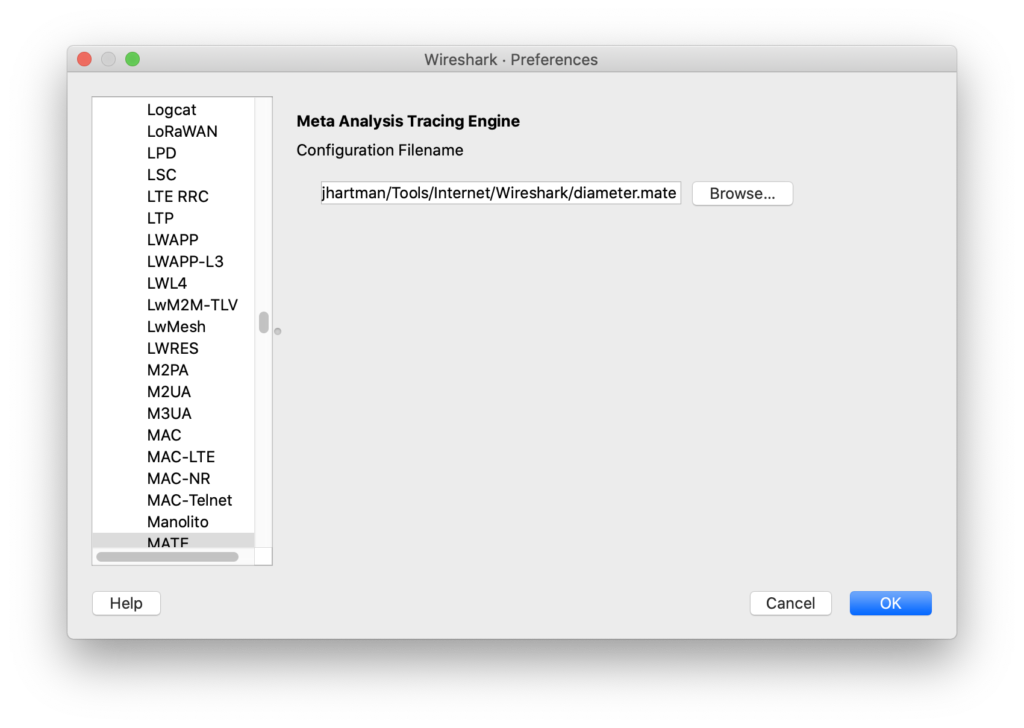
Configure Wireshark
Wireshark protocols configuration set this file under MATE:
Now a new protocol tree MATE should appear in each Diameter Packet details. You can use these pseudo-AVPs for filtering.